Unauthorized Access on Public Static IP Addresses
Any network device is potentially vulnerable to unauthorized login, and you should take appropriate security precautions to protect access to the RediGate. This is particularly true if your RediGate has a public static IP address, where it may be vulnerable to repeated hack attempts via bots crawling the Internet looking for open IP addresses. The following suggestions are given for a few security precautions.
You should always consult with your IT department for security recommendations before placing the RediGate or any device in a mission critical application.
Change Password
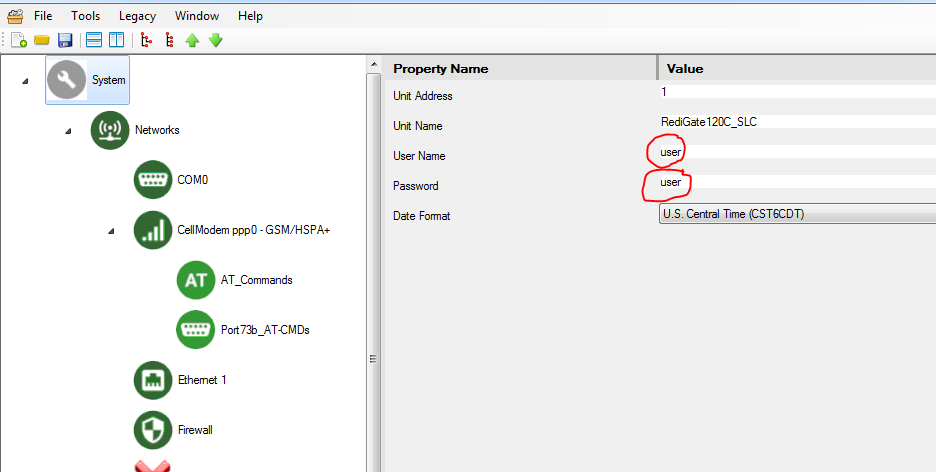
The easiest way to prevent unwanted logins is by changing the username and password in the "System" object to something more secure than the default value:
In general, you should regularly update both the user name and/or password, and the 'root' password, particularly if the RediGate is operating on a public network.
See RediGate User Accounts for a description of the standard login accounts on the RediGate.
See Changing the Root Password for information on setting the administrative password through the command line.
Check for Unauthorized Logins
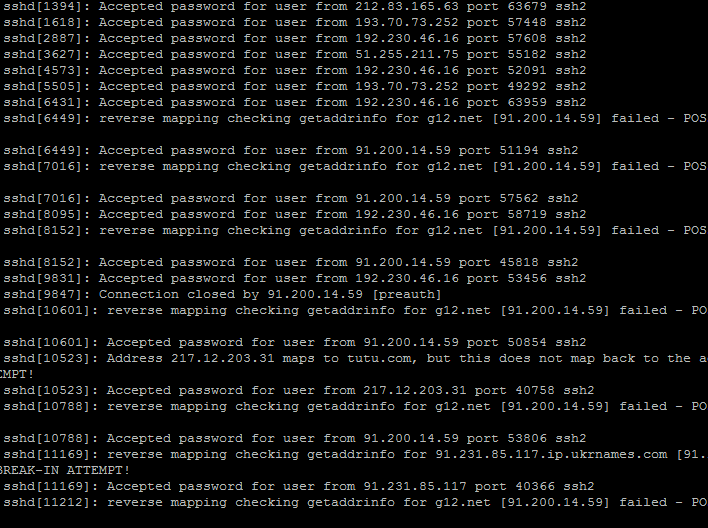
To check if your RediGate is experiencing unauthorized login attempts, login to the RediGate as the 'root' user and run the following command: cat /var/log/auth.log
This screenshot shows the auth.log file of a RediGate experiencing unauthorized logins:
Configure Firewall
It is highly recommended for any system, but especially for those on a public, static IP address network, to configure the firewall.
See RediGate Firewall Configuration for details on RediGate port usage and setting up firewall rules.
With the firewall, you can:
- Block or Limit Access to Specific Ports
- Block or Limit Outbound Connections
- Block Repeated Password Attempts
- many other options
Block all SSH, Use VPN Instead
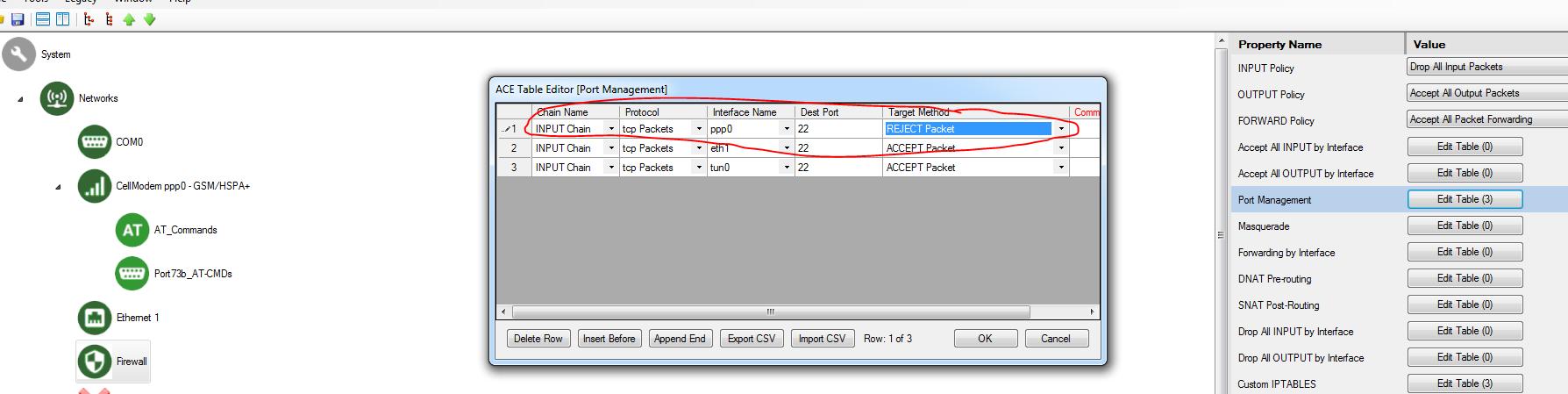
Another option is to block all access to port 22 on the public ppp0 interface using the Port Management section of the Firewall object in your ACE configuration:
In the configuration above, port 22 access is blocked over the public cellular network (ppp0), but allowed over the VPN connection (tun0).